How to get ISO 27001 Certification
Getting ISO 27001 certification can be a complex process and challenging for any business not quite prepared for the audit. Organisations often fail to fully understand how the standard translates into real-world security control implementations, and what is needed to gain that all important approval from the assessor.

The most important thing to understand is that to be certified, an approved ISO 27001 assessor needs to review your information security management system and agree that you meet all the minimum requirements. You must demonstrate your organisation’s compliance against each of the in-scope controls, which must be supported by operational evidence that you are using the controls.
Preparing your Information Security Management System
Before applying for certification, you will need a compliant Information Security Management System (ISMS) that allows the auditor to cross-reference your ways of operating controls against those specified in the standard. This ISMS is your management system, which tells your staff how they should undertake security activities and records audit trails of decisions and outcomes of security processes.
Once you have the ISMS integrated into your overall business management systems, certification follows across three main phases:
- Engage an assessment organisation that can audit your ISMS and issue your certification if you pass the assessment. They will begin with a basic review of your ISMS documentation, looking at the overall structure and documented processes covering all relevant controls. This assessment will identify the gaps that need remediating before you invest in a real certification audit.
- When ready, the certification organisation performs a more in-depth audit, where individual control elements of ISO 27001 are checked against the documentation in your ISMS. Evidence must be shown that policies and procedures are followed, and all teams understand the controls and requirements as relevant to their roles. A lead auditor will be assigned and will be responsible for awarding the certification.
- Follow-up audits can be scheduled between the certification body and your organisation should certain remediation be needed to gain certification. In some cases, the organisation is too far away from being certifiable, and they need to undertake a large programme of work to address the gaps. In this case, they need to start back at phase
If you gain your certification, you still need to maintain the ISMS in a certifiable form. Annual maintenance reviews (also known as surveillance audits) occur to check that you remain compliant. If something has slipped and is no longer compliant, the maintenance audit identifies these issues and allows you a grace period to remediate them. If they are not addressed, it is possible you may lose your certification.
Introducing the ISO 27001 Standard
Make sure you familiarise your primary stakeholders with the standard and how each section is arranged so that everyone understands what they are expected to do. The standard is made up of 12 separate sections, as follows:
| Introduction | What information security is and why it’s important to manage security risks. |
| Scope | Explains the extent to which the ISMS is implemented and its applicability across the business. |
| Normative References | The relationship between ISO 27000 and ISO 27001, and any other referenced standards important to its implementation. |
| Terms and Definitions | The terminology used within the standard. |
| Context of the Organisation | Lists the stakeholders involved in the creation and maintenance of the ISMS. |
| Leadership | Explains how stakeholders should commit to ISMS policies and procedures and encourage uptake across the rest of the business. |
| Planning | A project artefact that shows how risk management should be planned and executed across the business. |
| Support | Explains methods used to raise awareness about information security and assign responsibilities to stakeholders. |
| Operation | Details how operational risks are managed and how documentation should be performed to meet operational audit standards. |
| Performance Evaluation | Guidelines on how to monitor and measure the performance of the ISMS. |
| Improvement | An ISMS needs to continually improve, so this section explains how this process works in your business. |
| Reference Control Objectives and Controls | An annex detailing the elements of an audit. |
The ISO 27001 standard breaks down security best practices into 14 control categories, with each having several controls that must be implemented to claim compliance. ISMS controls are met through a combination of roles, processes, and technology systems and are categorised as follows:
- Information Security Policies – How policies and processes are written and reviewed for compliance. Auditors will look to see how complete your documentation is and when it was last reviewed.
- The organisation of Information Security – This describes which elements of your organisation are responsible for security activities. Auditors will expect to see a clear organisational chart with high-level roles and responsibilities linked to documented ISMS processes and procedures.
- Human Resource Security – Explains how employees are informed about cybersecurity when joining or leaving your organisation, or when they change roles. Auditors will require clearly defined security procedures for onboarding and offboarding.
- Asset Management – The processes involved in managing data assets will be assessed by the auditor, who will want to see how they are secured and accessed. Auditors will check to see if you keep accurate logs of hardware, software and databases. Evidence will be necessary for the auditor and must include common tools or methods used to assure data integrity.
- Access Control – Explain how employee access is limited to different types or classifications of data or limited to specific systems or services. Auditors will require detailed documentation that explains how privileges are awarded and who is responsible for maintaining them.
- Cryptography – These are the practices used by your business for encryption. Auditors will look for evidence that your systems handle sensitive data securely and you are using strong, reputable encryption algorithms.
- Physical and Environmental Security – This section covers the processes and procedures for securing facilities such as buildings, offices, and extends coverage to include your equipment. Auditors will look for vulnerabilities in your physical security, including how access to offices, loading bays and data centres is permitted.
- Operations Security – Guidance on how to collect and store data securely and run security systems to protect the business. Auditors will seek evidence of data flows and examine your documentation relating to how your operational activities work. They may also request specific assurance tests of your systems, such as a vulnerability assessment or penetration test.
- Communications Security – This category of controls includes the security of data transmission across the organisation’s network. Auditors will assess the communication systems you use, such as email or videoconferencing, and look at the implemented controls you use to keep that data secure in transit across your networks.
- System Acquisition, Development and Maintenance – These are the processes for managing the security of development projects, including security development environments and testing environments. Auditors will seek evidence that newly transitioned systems adopt the appropriately high levels of security that the rest of your business uses.
- Supplier Relationships – This section looks at how organisations interact with third parties while ensuring security remains enforced through that supply chain. Auditors will review third party contracts with outside entities who may have access to sensitive data.
- Information Security Incident Management – Incident management covers the best practices for how to respond to security events or alerts. Auditors may require you to run a drill to see how you handle an incident within your organisation.
- Information Security Aspects of Business Continuity Management – This stage of the review covers the analysis of how you handle business disruptions and major changes. Auditors may examine your processes using a tabletop exercise to discuss theoretical disruptions. They will expect to see playbooks that you will use to recover from the disruption while maintaining security.
- Compliance – The final section focuses the auditor’s review on government or industry regulations and ensures you are in compliance with those requirements. In Australia, this may include ACSC’s Essential 8, or a local state-based assurance framework like the Victorian Protective Data Security Standards.
A misstep many organisations make is placing responsibilities for ISO certification on the IT team. Although information technology is at the core of ISO 27001, the processes and procedures are shared across the business and must be championed by someone with the authority to make sure all teams are following the guidelines.
When preparing for an ISO 27001 audit, it is recommended that you seek assistance from someone with compliance experience, as audits are expensive, and delays or failures may set you back many months.
How to maintain ISO 27001 Compliance
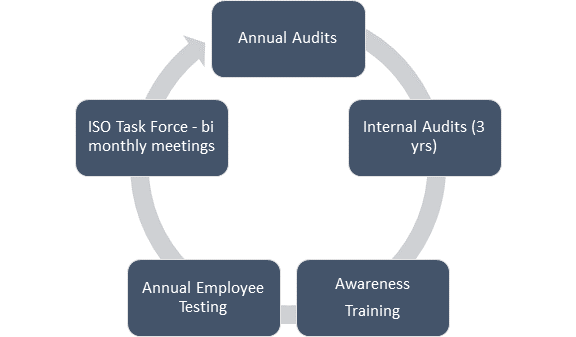
Gaining your initial ISO 27001 certification is a great step towards full compliance. However, the next step is ensuring that after the implementation project you maintain these high standards. Oftentimes, once the audit has passed, employees may begin to cut corners or not be so diligent in following procedures. If new employees are hired into the business on a regular basis, for example, the knowledge gained through the implementation programme can become diluted. Therefore, you should insist on regular (maybe quarterly) briefing sessions so that new staff understand the ISMS and existing staff are reminded of their responsibilities.
Organisations should conduct internal ISO 27001 audits as often as makes sense. We recommend doing it annually to reinforce risk management practices and look for gaps, but some organisations prefer to follow a rolling series of audits across different parts of their business each month. If you are reviewing your ISMS, then you should be ready for the next certification audit.
Form a working group with senior stakeholders to meet monthly and review the risk register, any actions or issues from operations and consider updates and improvements to the ISMS. One useful outcome from running this kind of working group is the development of a compliance tailored checklist you can run through prior to your next audit. An example might look something like this:
- Have you lined up management support for ISO 27001 activities?
- Have the scope for the ISMS been defined and have stakeholders been appointed across the organisation?
- When was the last time the security policy was reviewed? Is it up to date?
- Is the organisation’s risk assessment methodology up to date and socialised across the business?
- Do staff report, assess and manage risks via the organisation risk management process?
- Do you have a Statement of Applicability for the ISO 27001 controls which are applicable?
- Do you have a risk treatment plan so that stakeholders know how to treat risks?
- How do you measure controls efficacy and are these measurements captured and accurate?
- Are all controls Implemented and effective?
- Do you have a security awareness training programme that extends to all individuals across the business?
- Are you monitoring the ISMS to understand whether it is used, and procedures are followed?
- Have you conducted internal audits to assess ongoing control compliance?
- Have audit outcomes been reviewed with senior management and security stakeholders?
- Have you dealt with any incidents and shown how your organisation learns from each event?
How Sekuro can help
Sekuro is happy to discuss the ISO 27001 certification process with you and help you prepare your ISMS or prepare your evidence for a certification audit. We specialise in IT governance, risk management and compliance services, and have experts who work as ISO 27001 security managers, auditors, and assessors.

