ACSC essential eight
What is the ACSC Essential 8 (E8)?
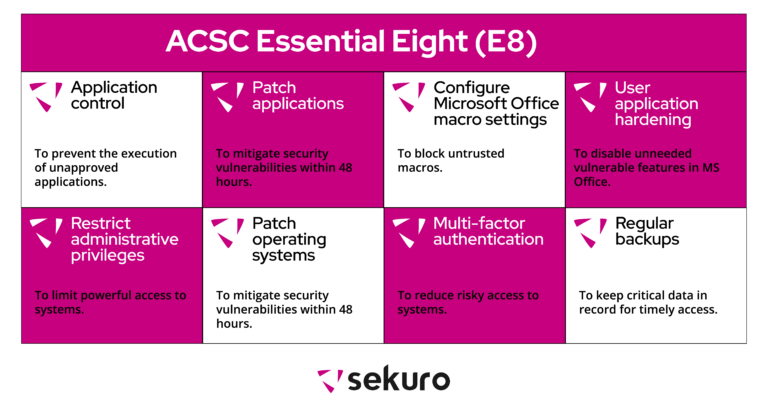
ACSC Essential 8 Controls and their Importance:
The Essential 8 strategies focus on 3 key objectives for mitigation strategy. The infographic below explains each of the mitigation strategies, the controls, and the importance of these controls:
Effective implementation of these controls is a starting point, and continual improvement to bring maturity is key in keeping up with the changing cyber threat landscape. Once the baseline controls are implemented, organisations should focus on increasing the maturity of their implementation such that they eventually reach full alignment in keeping the intent of each mitigation strategy.
ACSC has defined three maturity levels to assist organisations in determining the maturity of their implementation. The maturity criteria defined in ACSC Maturity Model includes:
- Maturity Level 1 – Partly aligned with intent of mitigation strategy.
- Maturity Level 2 – Mostly aligned with intent of mitigation strategy.
- Maturity Level 3 – Fully aligned with intent of mitigation strategy.
Sekuro’s ACSC Essential 8 Maturity Assessment Approach
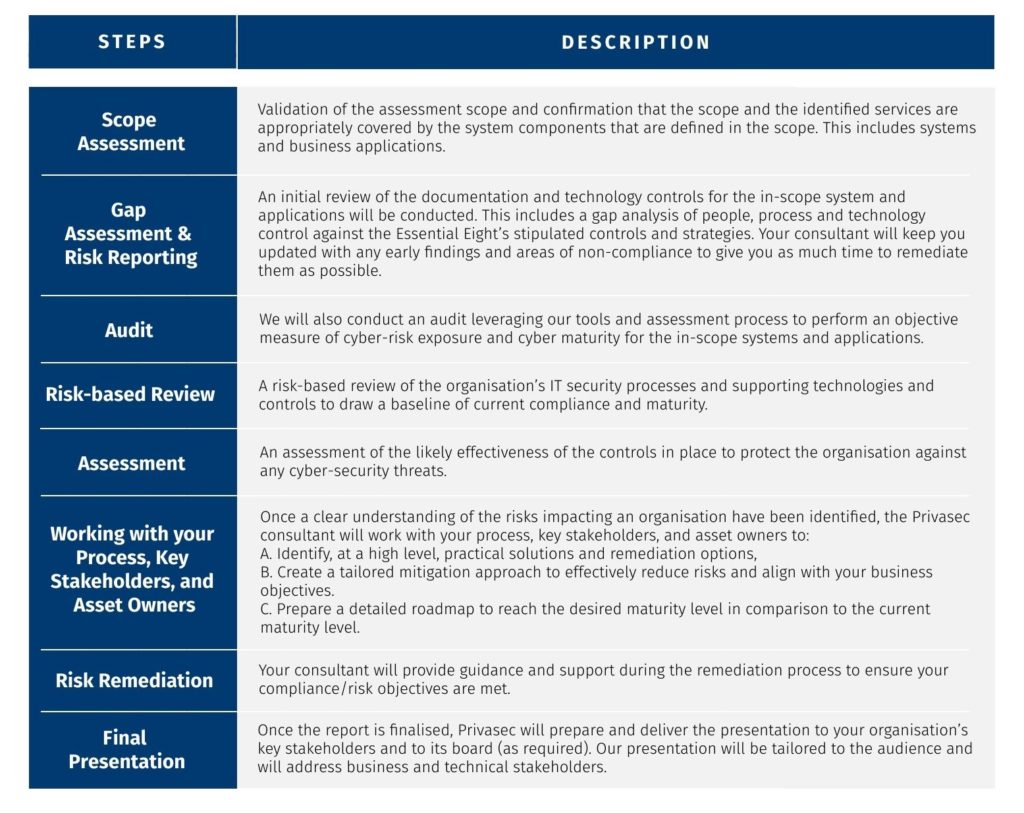
Sekuro follows a mature assessment and auditing approach to provide organisations with assurance on its effective alignment with the Essential 8 controls and roadmap to achieve the highest level of maturity.
Our assessment process leverages the people, process, and technology aspects with a combination of advanced auditing tools to provide an objective assessment of risk and compliance to the Essential 8 controls.
Deliverables
Our reports provide a holistic and detailed view of the organisation’s current compliance to the Essential 8, cyber-risk exposure profile and the current maturity. We also deliver a detailed compliance roadmap against each of the mitigation strategies, with recommendations of ways to achieve the highest level of maturity.
These reports form a baseline for the Annual Compliance Reporting and can be used to support the organisation’s cyber-security reporting, for example, NSW Cyber Security Policy Annual reporting and attestations submissions to relevant governance bodies including the Cyber Security Senior Officers Group (CSSOG) and the ICT and Digital Leadership Group (IDLG).
