“Critically, retailers need to implement a Zero Trust approach to security to remain competitive, and keep their staff and customers safe from cyber crime. A strong cyber security posture is critical for business enablement. Without it, retailers risk losing customers, damaging brand reputation, costly litigation and a halting of trading.”
In an article published for RetailBiz, Sekuro’s Customer CISO Lee Roebig expounded on the importance of aligning a security program with Zero Trust for stronger business resilience, in a time where organisations are experiencing exponential volumes of cyber attacks.
The Current Situation
In today’s highly digitalised world, shopping for goods and services has never been easier. With the rise of online shopping, many retail businesses have shifted online to expand their customer base. However, this entails increased exposure to cyber risks, where cyber security management is critical to defending against the multitude of online scams that threaten to steal customer information.
This is especially so with consumers providing a significant amount of their personal and financial information to online retailers for transactions, which makes the industry highly attractive for cybercriminals. According to an article by Insurance Business Australia, “Australians have already lost over $1.8 million to online shopping scams by the first quarter of the year alone.”
The importance of Cyber security
Data breaches and, by extension, online shopping scams affect not only individuals but also businesses. In the event of data breaches, companies often lose the trust and support of customers who have had their data stored in the company stolen, and this translates to direct financial impact for the organisation. This is corroborated in past statistics such as the Comparitech report, which states that “organisations who suffer a data breach underperform 15.6% on average over the subsequent three years.”
Hence, Lee made a call for retail businesses to recognise the importance of cyber security and to take concrete action to strengthen their security systems – and one effective way to do this is to adopt a Zero Trust approach.
“While we cannot stop the retail industry from being a lucrative target for cyber criminals, retail businesses do have the power to adopt strong preventative measures and conduct regular assessments of online platforms to protect customers.”
How Zero Trust Can Strengthen Cyber security?
Businesses can ensure both business agility and the enhancement of defenses by aligning with Zero Trust. In a simple definition, Lee referred to Zero Trust as “taking the stance that nothing should be trusted until proven otherwise.”
This approach to security requires companies to constantly re-assess users, applications and systems and decide whether they should be given permission to carry out an action. With that, businesses can proactively mitigate the risks of a data breach or cyber attack, where security controls are built on the assumption that an attacker is within the system at any time.
How Businesses Can Adopt the Zero Trust Approach
To help companies apply the concept of Zero Trust to their existing business operations, Lee introduced eight key pillars to consider: People, Identities, Endpoints, Networks, Infrastructure, Applications, Data, and Analytics.
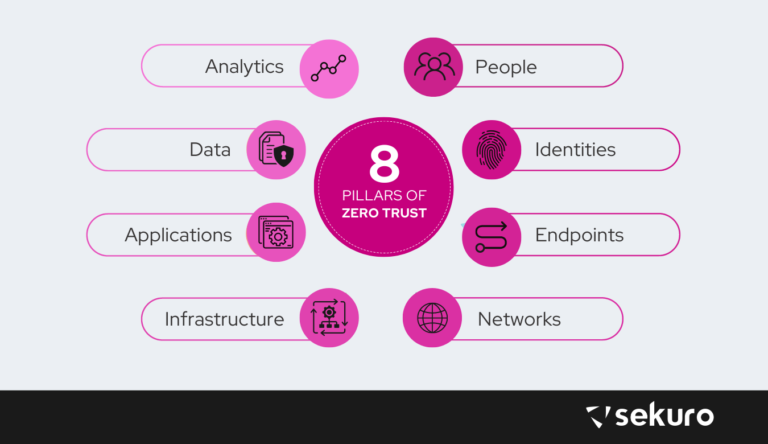
The 8 Pillars of Zero Trust
Even though building a Zero Trust model from scratch may sound daunting, Lee provided six key strategies to help businesses get started:
- Enroll all staff in strong security training. This will provide them with the right knowledge and tools to defend against cyber attacks. Re-assess the effectiveness of the training regularly by conducting continuous social engineering and phishing tests.
- Protect email services with configurations: This will block links that trick staff into entering malicious websites or opening unsafe attachments. These configurations could include an indication of External emails or quarantining emails with significantly similar names/addresses to internal staff. Additionally, incorporating email protection best practices into cyber security training is key to mitigating the chances of compromise due to human error.
- Safeguard your external attack surface by using tools/processes like web application firewalls, continuous external security scanning and secure software development practices. This will help protect your main external attack surface by strengthening the security of your web applications. Additionally, enhance protection of employee accounts by enforcing multi-factor authentication and strong password policies for your internal staff & contractors.
- Incorporate strong network segmentation practices by applying the least privilege on your network, limiting communication between users, servers and applications that do not need to communicate. This prevents the likelihood of a single compromised device leading to a company-wide breach.
- Utilise tools on your user/server endpoints like application control, endpoint detect and response (EDR) and real-time, cloud aware web filtering to protect your company against ransomware, data leakage and malware attacks. These tools should be cloud-controlled, which allows them to be equally effective off-premise and on-premise, anywhere in the world.
- Place a dedicated, monitored email address for disclosing vulnerabilities on your websites, plus offer & encourage multi-factor authentication to protect your customers’ online accounts. This shows your customers how much you value security, and how you will use it to protect their data.
Conclusion
Retail businesses need to protect their staff and customers from the constantly evolving threats. By adopting these recommendations, and aligning with a Zero Trust strategy, organisations can stay ahead and build a robust cyber security posture where security controls are in place to protect systems and users against all levels of risks.

Lee Roebig
Customer CISO, Sekuro
Lee is an experienced Cyber Security professional with 16+ years in the technology Industry. He has previously worked in cyber security leadership and architecture roles inside multiple global organisations prior to joining Sekuro. At Sekuro, Lee helps clients with Cyber security strategy, Zero Trust, Virtual CISO, mentorship, executive advisory and security architecture. He has worked with numerous clients on cyber security strategies across industries such as health, insurance, construction, manufacturing, leisure including multiple ASX listed companies.

