Limited visibility and under pressure
The expanding complexity of the attack surface and the sophistication of modern attacks that mimic legitimate behaviour strains organisations, making it challenging to maintain visibility and manage security. Security teams are under immense pressure to detect, respond to, and contain threats, a task made daunting by the sheer volume of alerts and the need for comprehensive analysis of all activities. This continuous demand heightens the state of alert, risking oversights and escalating the potential for breaches.
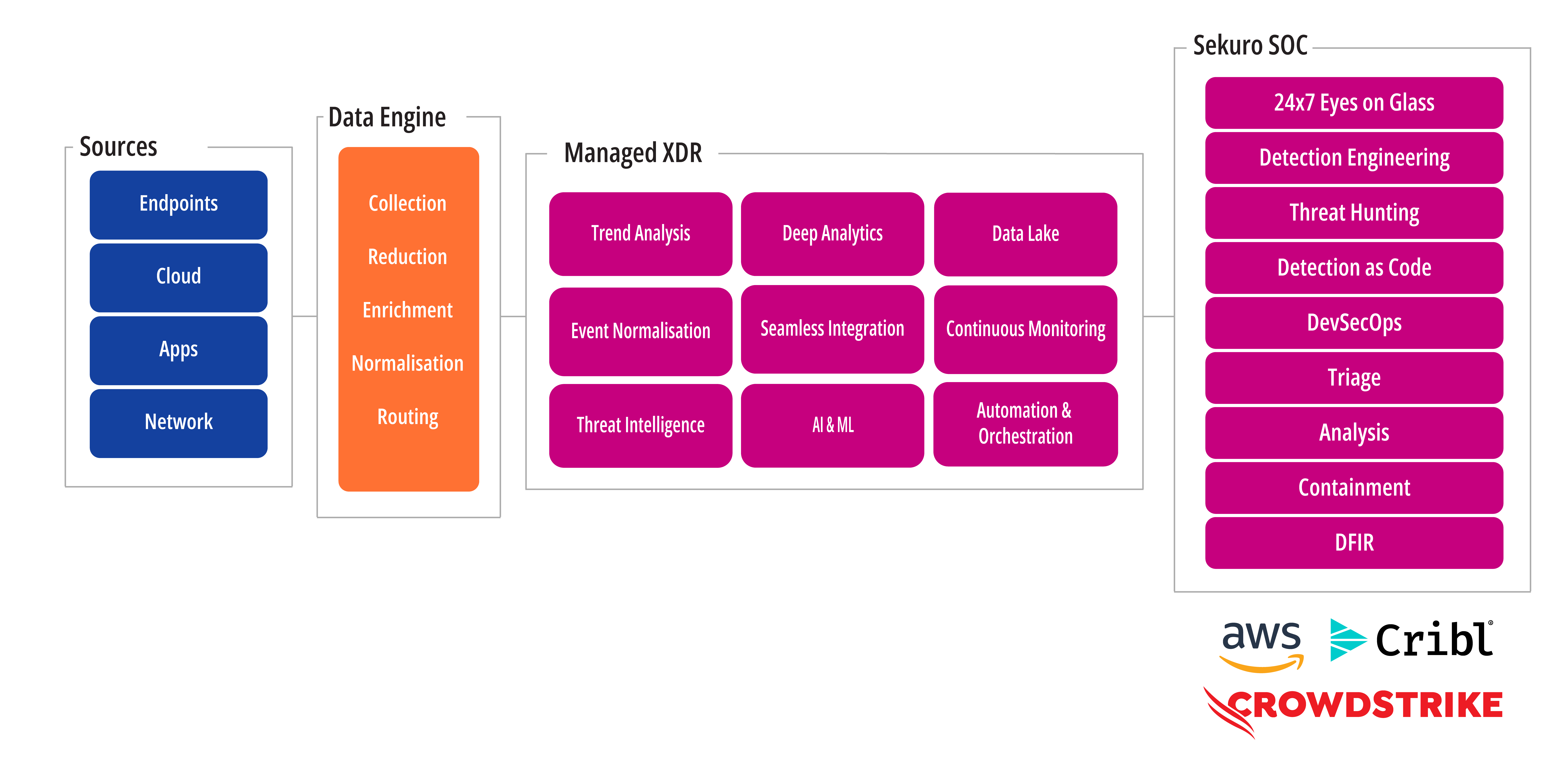
MANAGED XDR by Sekuro
Managed XDR is a comprehensive security solution delivered as part of our managed security service which operates 24/7, providing your organisation with expert-driven threat hunting, monitoring, investigation, and response capabilities to secure your entire attack surface. By correlating both native and third-party telemetry data to provide more context, organisations gain enhanced visibility across various domains and comprehensive threat remediation.
Initiating the deployment, managing the platform, and providing response and remediation services to tackle advanced threats are all part of our solution. This is accomplished without the need for your organisation to deploy and manage a 24/7 security operations function on your own.
Key Benefits of MANAGED XDR
- Detect and Eradicate Threats Faster: Faster response and effective mitigation are enabled as events are correlated and contextualised.
- Prevent Business Disruption: Business operations continue uninterrupted as attacks are proactively neutralised.
- Transform Alerts into Action: Focus on critical events as Managed XDR converts overwhelming alerts into clear and actionable insights.
- Accelerate Decision Making: Security decisions are orchestrated and automated at the right time for triage and investigation.
How it works
We collaborate with your organisation’s security and business stakeholders to identify your business goals, evaluate your security needs, onboard our team, and integrate Managed XDR with your organisation’s data sources. When an alert is triggered, the Managed XDR Platform automatically correlates data from any source, including cloud, network, application, and endpoint, into a unified, context-aware alert, triggering our initial investigation.
The platform gathers all forensic artifacts and processes them for an in-depth analysis by our expert team of threat hunters. Through our security dashboards, they gain insights on the status of detection, monitoring, triage, investigation, and threat hunting across the entire environment, all viewed through a single interface.
| Service Component | Description |
|---|---|
| Detection and Incident Management | Continuous detection, prompt triaging, thorough investigation, efficient containment, and effective remediation of security incidents to ensure timely and robust response to potential threats. |
| Data Sources and Use Cases | Rapid systematic development of use cases using a predefined methodology, identification of relevant data sources, and integration with threat intelligence efficient and meaningful data analysis and insights. |
| Threat Hunting | Proactive development of hypotheses, identification and investigation of potential threats, comprehensive reporting, and diligent follow-ups to detect and mitigate security risks before they escalate. |
| Threat Intelligence | Leveraging intelligence driven advanced search queries in the SIEM to analyse and derive meaningful insights from data, enabling informed decision-making and proactive problem-solving. |
| Dashboards and Reporting | Ensures real-time access to data that is both insightful, and actionable by key stakeholders. |
| Platform Support and Updates | Ongoing maintenance and support for managed components of the service and to remotely update client-side data engine components. |
| Continuous Service Improvement | Improvements based on ever evolving business requirements and Sekuro research and development. |