By Sekuro Hackcelerator 2021 Mentee, Martin Hossain
Since 2020, ransomware attacks have increased. Amongst other countries, Australia has fallen victim with the ACSC reporting that within the 2020-21 financial year, there was a 15% increase in ransomware reports. [1]
Home Affairs minister Karen Andrews, stated that such attacks are multi-faceted, affecting everyone from unsuspecting individuals, to critical infrastructure frameworks including in the electricity and healthcare sectors. [2] COVID-19 has recently been identified as the most common culprit for ransomware, as society migrated towards a digital environment, with 63% of Australian organisations reporting that their remote working and digital transformations have exposed them to ransomware attackers. [3]
So how does this apply to you?
As Andrews mentioned, ransomware affects all parties in the cyber-world. As an individual, you are more susceptible to ransomware attacks as you lack the resilience of an organisation, and when users are without proper education and awareness of how to counter ransomware, attackers can financially thrive.
This blog can help you discern between harmless communications from legitimate companies and suspicious emails or texts. This is because malware can be masqueraded as a regular message, and once it activates, it blocks access to your files, requiring payment for its release. [4] This blog will provide pre-cautionary safeguards against potential attacks, because despite you being able to pay off the ransom, there is no guarantee that the attackers will unlock your files, as reported by a recent Forbes article where 92% of people who pay end up not recovering their data. [5]
Email Ransomware
While emails have long been a popular method of communication, ransomware can unknowingly be installed by email users, primarily through email phishing. Phishing aims to deceive the user through clickbait emails involving, for example, winning a money prize through a contest, false bank statements requiring login credentials or when you have an online purchase with requests for updating your payment details. [6] These examples take two forms of email ransomware: Crypto and Locker ransomware. Crypto uses complex encryption to cover all files requiring a key for decryption, and Locker involves complete denial of access to the computer. Both will restrict your personal data and will be dangerous if one holds sensitive information. [7]
It is important, especially during the COVID period, to be aware of fake emails. This is because in the first quarter of 2020, there was a 600% increase in COVID-related phishing emails, with a 30% or higher success rate. [8] Many people may be under financial stress, which can impair their judgement and such people may end up clicking on ransomware links. In order to be safe, there are five ways to check:
· Ensure that your anti-virus and malware software is turned on and functioning
· Look for malicious or out of place URLs
· Check the email address against the official body (e.g., ATO)
· Incorrect spelling or out-of-place words
· Check for urgency in emails (e.g., your account will be suspended if you do not respond). [9]
These pre-emptive steps will benefit each individual and deter cybercriminals from such activity.
text messages
A recent trend affecting many Australians involves spam calls and texts which have ransomware links. Since we live in a world where phones are widely available, cybercriminals can manipulate more people through spam calls and messages, arguably more so than emails.
Dodgy text messages have raised suspicion towards ransomware, with messages being sent from randomised mobile numbers. An example involves the FluBot scam, which takes the form of perpetrators impersonating legitimate businesses, notifying victim by text that they have a voicemail, or missed a call, or have a package delivery. [10] To many people this can be an instant give away as voicemails and package delivery systems do not operate solely on text messages, but being that there are over seven billion of us, there are bound to be successful scams. A 9 News report highlighted that since August this year, the ACCC received over 16,000 spam reports, with victims collectively losing over $236 million. [10]
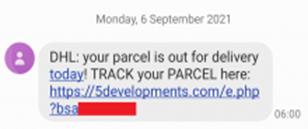
Example of a FluBot text message
Source: https://www.scamwatch.gov.au/news-alerts/missed-delivery-call-or-voicemail-flubot-scams
Many may believe that the above image is legitimate, as some poor victim is actually expecting a package. However, this proves that human agency in technical environments tend to be the weakest link, which therefore requiring up-to-date education. [8]
Where ransomware prevails, it is best to back-up your data prior and factory reset your phone, according to CERT NZ. [11] You can invest time and experience in software specific techniques for Android and Apple systems, with the former proven to be effective in preventing ransomware damage through existing information patterns and processor data without needing to read the ransomware directly, minimising damage. [12]
Overall, a combination of common sense and general awareness of how ransomware works through displaced links, inconsistent messages and confirming origin of sender will increase your safety.
Sekuro's ransomware readiness assessment
Simulating real-world Tactics, Techniques, and Procedures (TTPs) utilised by ransomware adversaries and cyber-criminal organisations to compromise and deploy ransomware throughout corporate Windows environments, Sekuro’s Ransomware Readiness Assessment enables your organisation to understand gaps and remediate ransomware exposure risk with this common and growing risk.
related post:
What is IoT and what are its security and legal issues?
references
[1] https://www.paloaltonetworks.com/blog/2021/10/australias-ransomware-action-plan/
[2] https://www.theguardian.com/australia-news/2021/oct/13/cybercriminals-to-face-new-offences-as-ransomware-attacks-grow-in-australia
[3] https://securitybrief.com.au/story/rate-of-ransomware-attacks-in-australia-well-above-global-average-report
[4] Almomani et al. 2021, ‘Android Ransomware Detection Based on a Hybrid Evolutionary Approach in the Context of Highly Imbalanced Data’, IEEE Access, vol. 9, no. 1, pp. 57674-57691.
[5] https://www.forbes.com/sites/daveywinder/2021/05/02/ransomware-reality-shock-92-who-pay-dont-get-their-data-back/?sh=1f0412bae0c7
[6] https://www.securitymetrics.com/blog/top-10-types-phishing-emails
[7] Suresh et al. 2019, ‘Detection of Ransomware in Emails Through Anomaly Based Detection’, in DJ Hemanth et al. (ed.), Emerging Trends in Computing and Expert Technology, Springer, New York, pp. 604-613.
[8] Pranggono, B & Arabo, A 2021, ‘COVID-19 pandemic cybersecurity issues’, Internet Technology Letters, vol. 4, no. 2, pp. 1-6.
[9] https://www.metacompliance.com/blog/what-is-a-ransomware-email-5-tips-for-how-to-detect-one/
[10] https://www.9news.com.au/national/australia-scams-estimated-15-million-aussies-have-received-a-fake-text-message-or-phone-call/c3a7e635-4cd9-4566-90c4-ce73cbad0185
[11] https://www.stuff.co.nz/business/127040465/single-mum-issues-warning-after-falling-victim-to-text-scam
[12]Song, S, Kim, B & Lee, S 2016, ‘The Effective Ransomware Prevention Technique Using Process Monitoring on Android Platform’, Mobile Information Systems, vol. 2016, no. 1, pp. 1-9.

