Operational Technology (OT)
OT threats on the rise
The way we build and maintain our infrastructure is changing. This is because operational technology (OT), like machinery, has converged with information technology (IT) to create smarter, more efficient systems. However, with this comes new risks. OT infrastructure and industrial control systems (ICS) no longer run in a closed and isolated system, and where there is connectivity, there are opportunities for attackers to exploit these technologies.
Society’s growing reliance on converged IT and OT systems within our critical infrastructure has left the backbone of our society vulnerable. Research from Dragos found cyberattacks targeting critical OT and industrial organisations rose by 87% between 2021 and 2022.
Cyberattacks on IT systems focus on exposing or withholding information for financial or personal gain, whilst OT cyber security focuses on protecting physical processes and machinery, where uptime and safety are critical.
What makes attacks on OT different is that they can impact not just our online environment but also our physical one through service disruptions, economic damage, threats to public safety, and even lives. From attacks on Smart City infrastructure to healthcare system sabotage, water treatment facilities, nuclear facility breaches and agriculture sabotage, the consequences of OT attacks can be downright terrifying.
Sekuro OT Capabilities
Whether you’re a utility company ensuring the lights stay on, a transport provider making sure trains run on time, or an industry organisation looking to fortify your OT systems, Sekuro is your trusted partner in securing what matters.
We possess a deep understanding of the significance of every cog in your operational machinery and the importance of defending OT systems. With this understanding as a foundation, Sekuro offers a comprehensive suite of services tailored to meet the unique challenges faced by anyone maintaining OT and critical infrastructure.
From assessing your current infrastructure and spotting weaknesses to designing robust and resilient systems, as well as monitoring and compliance with pivotal regulations, including the Australian 2018 Security of Critical Infrastructure (SOCI) Act, Sekuro has you covered.
- We understand the unique challenges and requirements for OT and critical infrastructure environments, including minimal disruption and high reliability, as well as navigating different protocols, form factors, and manufacturers.
- Our cyber security solutions enhance operational continuity and safety.
- As an end-to-end cyber security and digital transformation consultancy, our holistic approach has enabled us to build the leading business platform for OT convergence in the market.
- We enter every conversation with a consultative mindset, focusing on understanding each organisation’s specific challenges and needs.
- Our highly customisable subscription-based Cyber Resilience Program (CRP) is designed to enhance an organisation’s cyber maturity and reduce its cyber security risks, allowing immature organisations to step into the fold and get OT security that they might not have been able to before.
The cyber security industry has long worked hand in hand with IT professionals, yet there is a lack of understanding of how to engage with engineers managing OT technology. We support customers in finding a common language between cyber security professionals and the OT engineers designing and maintaining the incredibly complex environments, ensuring they have the threat context they need to implement a suitable OT security strategy.
Our partnership with Dragos
Securing the backbone of modern society isn’t just about deploying the latest cyber defence tools or patching vulnerabilities. It involves the intricate dance of understanding and safeguarding critical systems, mastering the nuances of OT stacks, and ensuring that every component functions in harmony, from top to bottom. It’s about the meticulous design and assurance of systems, continuous monitoring, and compliance with ever-evolving regulations. In Australia, this means navigating the intricacies of regulations such as the Australian SOCI Act. This is where Sekuro steps in.
As part of our commitment to curating our offerings in partnership with the world’s best vendors, we’ve partnered with Dragos, the industry’s most advanced OT cyber security platform, to strengthen our OT cyber security capabilities.
The Dragos Platform gives you visibility into your ICS/OT assets, vulnerabilities, threats, and response actions and supports you with forensics and OT-specific playbooks.
- Improve visibility of OT assets
- Defend against ransomware in OT
- Stay ahead of sophisticated industrial cyber security threats on a global scale
- Operationalise MITRE ATT&ACK for ICS
Sekuro’s partnership with Dragos will enable new and existing customers to get the most out of the Dragos platform by leveraging Sekuro’s expertise and support.
Sekuro’s approach to OT security
At Sekuro, we understand that the OT landscape presents unique challenges and requires a bespoke approach to cyber security. As specialists in securing critical infrastructure, we offer a comprehensive suite of services designed to protect your operations from the ever-evolving spectrum of cyber threats.
Our expertise spans Offensive Security, Governance, Risk, and Compliance (GRC), and Managed Security Services (MSS). Moreover, we take pride in facilitating our customers with the integration of the Dragos platform into their environments, thereby enhancing their cyber security posture and resilience.
When it comes to testing, our approach is distinct from traditional IT cyber security measures. Given OT systems’ often sensitive and mission-critical nature, our methodologies are designed to rigorously assess security without disrupting operational integrity. Unlike conventional IT environments, OT systems require a nuanced understanding of how digital networks interact with physical processes. Our testing strategies are, therefore, customised to address the unique challenges OT environments have. We recognise the potential fragility of these systems and adapt our testing to minimise any risk of impact, ensuring the safety and continuity of operations.
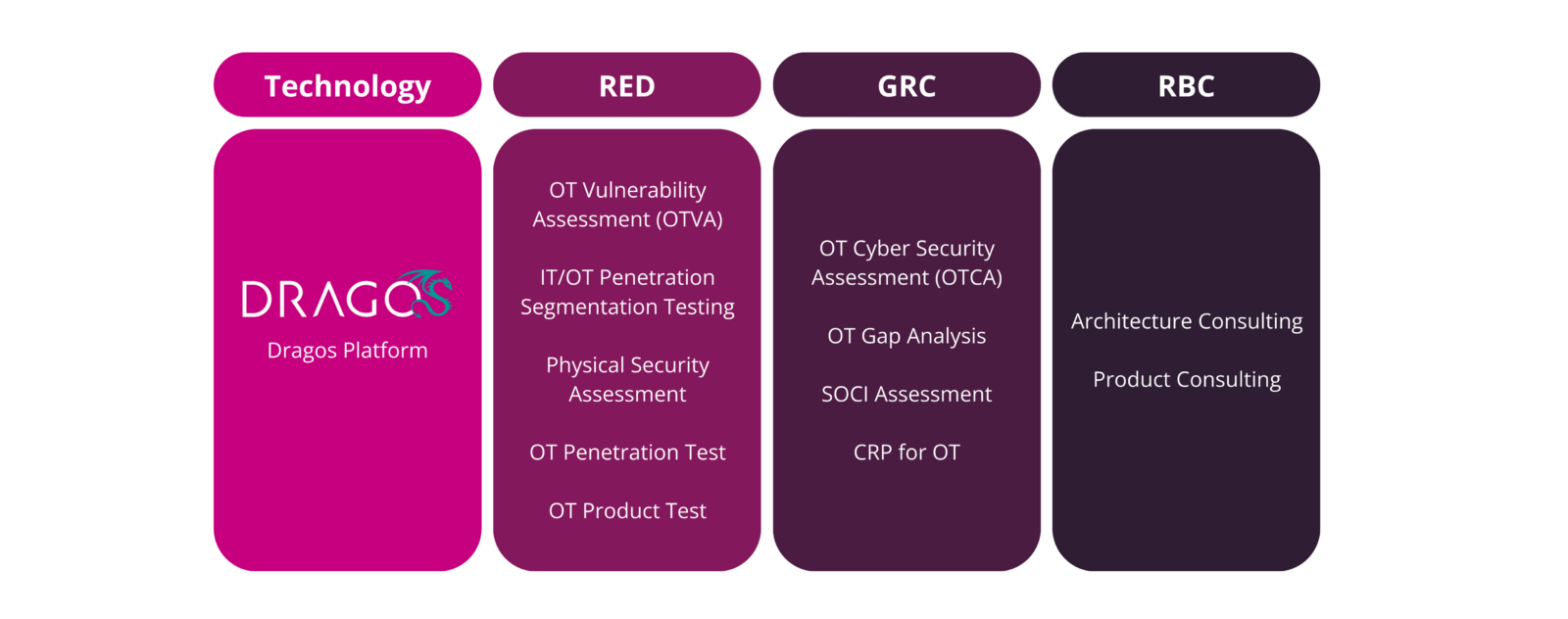
- Sekuro offers a robust suite of active and passive testing services designed to enhance the cyber security posture of OT environments. Our active testing capabilities focus on OT penetration tests conducted in lab settings or during scheduled maintenance to ensure minimal disruption to production environments. These tests rigorously evaluate OT products, including smart devices and communication platforms, for vulnerabilities in areas such as traffic handling, authentication, and platform communication.
- We take a passive approach to OT network assessments, conducting OT cyber security assessments (OTCA) and OT vulnerability assessments (OTVA) that offer a comprehensive review of your security from a people, process, and technology perspective. These evaluations include baselining exercises, program reviews, architecture analysis, and detailed assessments of host and application security. Our passive traffic analysis and physical security evaluations are designed to identify and address potential attack pathways and physical security gaps without impacting the network’s operational integrity.
- At the network perimeter, our active approach includes IT/OT penetration and segmentation tests, phishing simulation assessments, and other scenario-based methods to test the resilience of the network’s defences. Once access to the OT environment is achieved, we work closely with the customer to plan the next steps without active exploitation.
- Supporting regulatory compliance, Sekuro conducts SOCI assessments and OT gap analyses against standards such as AESCSF and NIST to ensure alignment with the SOCI Act and other critical industry benchmarks. Additionally, our OT tabletop exercises test an organisation’s response capabilities to cyber-attacks in OT environments, and we provide a Cyber Resilience Program (CRP) for ongoing OT environment maturity improvement.
Through this comprehensive testing suite, Sekuro not only demonstrates its high level of capability in assessing and improving the cyber security landscape of OT environments but also its ability to support organisations in maintaining compliance with industry regulations and standards.
Why choose Sekuro for your OT security?
Elite Expertise
At the heart of Sekuro lies a team of the industry's most seasoned security professionals. With a roster of experts who have sharpened their skills in real-world scenarios, we ensure our clients benefit from top-tier insights and techniques.
Strategic Alliances
Our world-class partnerships with leading tech companies and security innovators mean you don't just get our expertise – you get an entire ecosystem of technological innovation and security acumen.
Secure by Design
Recognising that every client has unique needs and challenges, Sekuro builds bespoke security architectures to precisely meet your needs. Our designs aren't just robust and resilient; they're tailor-made to fit your operational landscape, ensuring optimal functionality and protection.
Protective Monitoring and Response
In an era where regulations evolve, and threats dynamically change, Sekuro's SOC monitoring capability ensures you're always watching and predicting attacks before they cause any damage. Our retainer service affords you the surety that you're in good hands should the worst happen.
Compliance
Our GRC experts have intimate knowledge of the pivotal regulations and laws to which you must comply, including the Australian SOCI Act, and we can guide you to full compliance, shielding you from the potential fallout of failing an audit.
Frequently asked questions about OT
What is OT security?
OT, or operational technology, specialises in controlling and monitoring physical devices and industrial processes, ensuring real-time precision and reliability. OT security relies heavily on understanding how the sector (Energy, Manufacturing, Chemical Engineering, etc) using OT operates, and we do this by having thorough, two-way communication with the sector’s OT engineers.
Why is OT security important?
Cyber security in critical infrastructure is crucial because these systems are vital for its society’s functioning and security. A cyberattack on critical infrastructure, like power grids or water treatment facilities, can lead to severe consequences, including service disruptions, economic damage, and threats to public safety. Since OT is present in so many organisations, the SOCI Act has changed many organisations’ requirements for uplifting cyber security.
What is the difference between IT and OT cyber security approaches?
Although similar in many ways to standard enterprise information security, securing an industrial network presents several unique challenges. Industrial systems are built for reliability and longevity. The systems and networks used are easily outpaced by the tools employed by an attacker.
Systems in OT are often legacy ones, with a life cycle measured in decades rather than years. For example, it's not uncommon to find Windows 7 or Windows XP, which are obsolete, and therefore vulnerable, in IT environments. Given the emphasis on availability and the longer life cycle of these systems, updating an OS can sometimes bring down the entire process.
What is IT and OT Convergence?
There is a myth surrounding OT cyber security, suggesting that OT is entirely segregated from the IT world, requiring a completely different set of skills to assess and audit these environments. While this may have been true 20 years ago when OT environments were completely separated from IT, in recent years, different business needs have forced OT to become more "IT-ready." This shift has made OT environments more IT-like, incorporating typical IT components such as Windows servers, active directory, firewalls, etc.
What are my OT security requirements?
Despite the global infancy of OT cyber security regulations, Australia has taken proactive steps by introducing the SOCI Act, setting a precedent for legislative oversight. Alongside this, the Australian Energy Sector Cyber Security Framework (AESCSF) encourages entities to adopt a standardised security posture to be well-prepared against cyber-attacks. These initiatives reflect a commitment to strengthening the nation’s cyber resilience. For a comprehensive understanding of how these frameworks can be integrated into your cyber security strategy, contact Sekuro to discuss the optimal path forward for your operations.
What is best practice for OT security?
In OT cyber security, the convergence of IT and OT expertise is essential, blending their unique environmental insights to bolster defences. A best practice approach includes establishing a nuanced ICS Incident Response Plan, conducting ICS-specific tabletop exercises, reinforcing network architecture with strategic segmentation, and ensuring secure remote access. Enhanced visibility and proactive monitoring, coupled with Risk-Based Vulnerability Management, are also pivotal in pre-emptively identifying and mitigating potential threats to maintain a secure and resilient OT infrastructure.
What is the difference between IT and OT security?
OT cyber security focuses on protecting physical processes and machinery, where uptime and safety are critical. IT cyber security is about safeguarding data and information systems. What makes attacks on operational technology different is that they can impact our physical, not just online, environment through service disruptions, economic damage, and threats to public safety and even lives.
CONTACT US
We’ll give you a clear overview of availability and pricing and explain how our OT services can move your organisation forward resiliently.
Chat with a Sekuro consultant to get a clear overview of availability and pricing. Find out how Sekuro can raise your organisation’s OT resilience.
