In the 105th episode of the Get Cyber Resilient Podcast, Sekuro’s Customer CISO Lee Roebig joins host Garrett O’ Hara to share about his role in Zero Trust, helping organisations with cybersecurity strategy, risk advisory and associated technologies on their cybersecurity roadmap.
Lee has advised on Zero Trust strategies across a range of industries in Australia, including health insurance, banking, construction, manufacturing and multiple ASX-listed companies. Having accumulated 16 years of experience in what he calls the “non-consultancy side of the fence”, Lee has spent the majority of his career in the customer’s shoes and assuming leadership roles such as the Head of Information Security of a global APAC organisation.
Becoming Customer CISO of Sekuro
He proudly describes what he loves most about his role in the field of cybersecurity: “By protecting an organisation, you can potentially protect thousands of employees and millions of customers, and I think that’s a very rewarding part of the role.” The realisation — that joining a cybersecurity consultancy could allow him to protect people on a larger scale — inspired Lee to take on the role of Customer CISO in Sekuro.
Getting Into Zero Trust
Having previously been part of an organisation that had all its data in the company perimeters, Lee had what he described as a “rude awakening” when he moved to another organisation whose assets were all off-premise. As a result of remote working arrangements and a cloud-first technology strategy, there were no static IP addresses and domains, standard operating environments, images, workstations and services. Facing a sudden change in from what he was used to working with, Lee had to learn to adapt his cybersecurity program to embrace the technology strategy of the company, which tasked him and his team to come up with a strategy that would protect the company on a global scale without relying on internal networks and perimeter-based controls. After the strategy was well implemented with great success, he later found out that this modern approach to security he had been delivering had a name to it – Zero Trust – and has been advocating for it ever since.
With the evolving cyber risks, today's CISOs are required to innovate, adapt and look for new ways to improve their organisation's security posture. When done right, they will be able to enable new business/ technology initiatives without the added risks they once posed.
The concept of Zero Trust
When asked to define Zero Trust, Lee acknowledges that the concept cannot easily be summed up in a few words.
"Zero Trust refers to the concept that no one or nothing has access until it’s proven it should be trusted, and we must take as much context as possible into account before making that trust decision."
Lee's simple definition for those looking to understand Zero Trust at a fundamental level
He emphasises, that there is still a lot more to it. Zero Trust also involves the company’s mindset and approach towards cybersecurity – both now and in the future. Lee cautions against a misconception that many have regarding the concept of Zero Trust – the idea that it is a set of products that can be purchased from a vendor. Rather, Zero Trust is a type of mindset or philosophy that companies undertake.
How has the importance of Zero Trust in cybersecurity changed from the past to the present?
As explained by Lee, with the present advancements in technology, our organisation, its assets and data are externally accessible far more than in the past. Furthermore, due to a shift in working arrangements exacerbated by the Covid-19 pandemic, data is no longer contained only within the perimeters of the company. Instead, it is now accessible across through the public internet in many cases, which exposes it to many more threat actors. Further to this, our users and devices have also moved outside our perimeter, making our on-premise security controls like firewalls, network access control and others powerless to protect them. This is why a Zero Trust approach is vital for organisations that use remote working – it maintains the same level of protection, visibility and control even outside of the organisation’s perimeters.
What are the benefits of Zero Trust?
Zero Trust improves both employee experience and employee security. On the whole, a security programme enhanced with a Zero Trust strategy benefits both the organisation and its employees, increasing flexibility and productivity levels without the added risks.
Another significant benefit of Zero Trust is that it reduces the likelihood of burnout in security team members. Zero Trust shifts focus to be on prevention first rather than Band-Aid fixes and detective controls. In fact, a greater portion of security professionals’ work is now spent on more enjoyable and rewarding tasks such as identity and access management, network segmentation and application control, which focus on security architecture and collectively reduce the risk exposure of assets on the company’s network. According to Lee, this means much less time is spent on the historically more arduous tasks such as vulnerability management and non-stop patching, which have previously been a huge cause of collective team burnout. Lee reminded the audience that those things are still important, but their focus should be shifted in a modern Zero Trust strategy.
WHERE DOES ZERO TRUST FIT IN WITH POPULAR CYBERSECURITY COMPLIANCE FRAMEWORKS?
According to Lee, organisations often mistake compliance for security. Many companies become victims of data breach despite having spent an abundance of resources on attaining compliance. Lee offers an explanation for this: many companies’ compliance frameworks are overly broad and lack a clear end goal. Moreover, their reports provide very general findings that do not clearly specify the follow-up actions to take or what technologies to invest in to gain the desired outcome. Some organisations also treat compliance as the ‘final destination’, taking whatever shortcuts they can to achieve compliance outcomes. This leads to them stopping far shorter than they should and gaining a false sense of security. These greatly undermine the effectiveness of the frameworks put in place.
However, by incorporating a Zero Trust strategy into their frameworks, companies can shift their focus from simply being compliant to achieving stronger security outcomes using clearly defined controls.
Can smaller organisations benefit from Zero Trust too?
Even though the effectiveness of Zero Trust has had more recognition in larger organisations, Lee assures that it can also be used to the advantage of smaller organisations. In fact, although smaller organisations generally have fewer resources to implement a Zero Trust strategy, they are usually less complex in nature as compared to larger companies who have a more extensive network of users across several countries. This can make it easier for smaller organisations to achieve great outcomes in a Zero Trust strategy.
For a start, Lee encourages cybersecurity leaders to first examine the cybersecurity posture of their organisation and identify the areas they believe are the weakest link. To illustrate this point, Lee cites an example: if an organisation has excellent identity practices in place and is doing very well in people security, but is falling behind on the security of their internal network, it would most likely be a good idea to start by implementing a Zero Trust strategy in their internal network.
What does a practical approach to Zero Trust implementation look like?
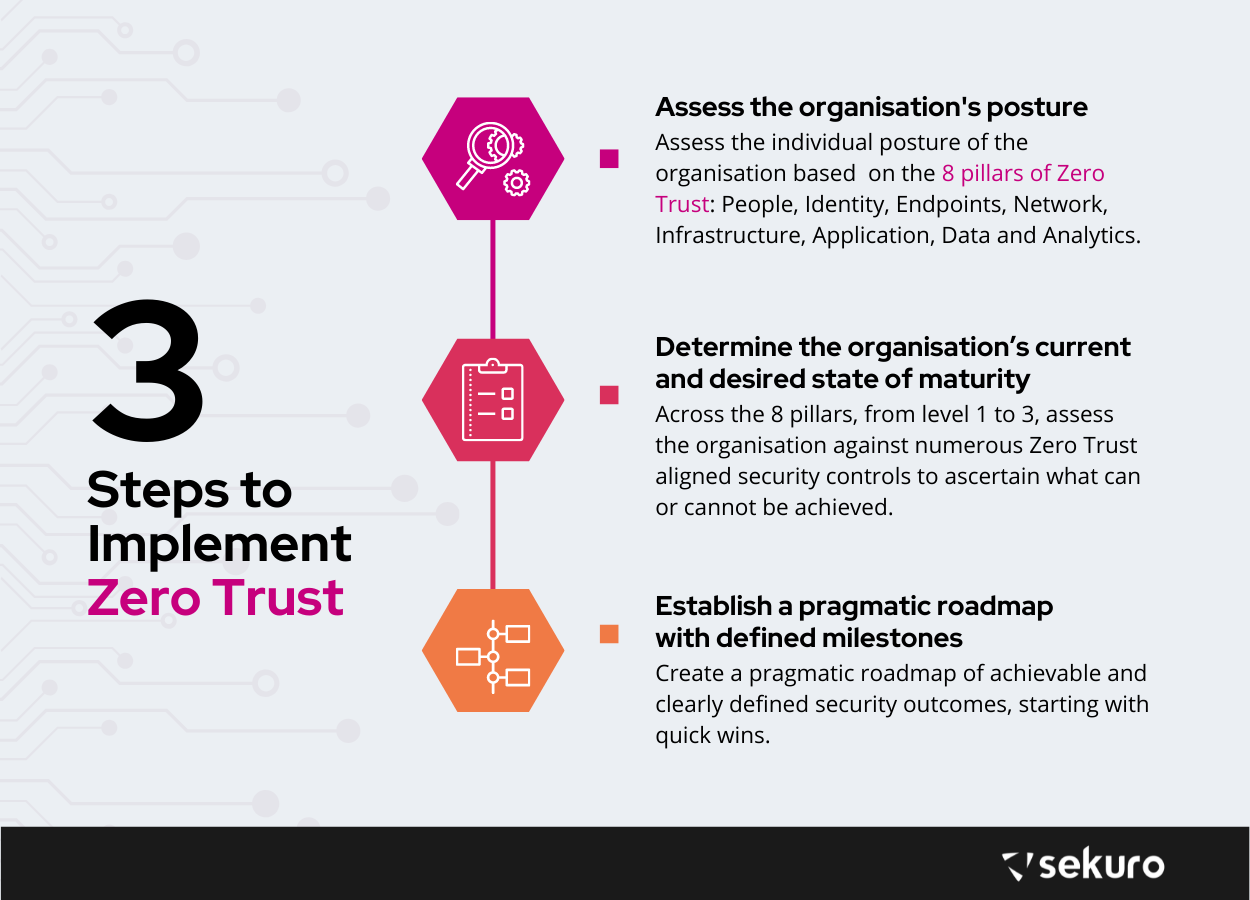
Lee’s high level guide to a step-by-step Zero Trust implementation involves the following:
- Assess the individual posture of the organisation based on Sekuro’s 8 pillars of Zero Trust: People, Identity, Endpoints, Network, Infrastructure, Application, Data and Analytics.
- Across the 8 pillar, determine the organisation’s current and desired future state of maturity (from levels 1-3) by assessing them against numerous Zero Trust aligned security controls to ascertain what is realistically achievable.
- Create a pragmatic roadmap of achievable, clearly defined security outcomes, starting with what can be done immediately (Quick Wins) and within 2+ years, broken down into digestible intervals of 6 months.
Aside from these steps, Lee highlights the importance of being as literal as possible when providing advice on Zero Trust, emphasising that it needs to remain actionable enough for organisations to follow.
Conclusion
While the concept of Zero Trust might seem foreign to those who are not well-versed in cybersecurity, organisations can equip themselves by first understanding the concept of Zero Trust, before actively seeking out professional advice tailored to their organisational needs.
Tune in to the full Get Cyber Resilient Podcast episode here.
Sekuro's approach to Zero Trust
Sekuro’s Zero Trust Strategy has been created by our team to zone in on the areas which provide the most prominent cyber security benefits, whilst being pragmatic and realistically achievable for all organisations. It was devised by cyber security professionals with years of hands-on experience in cyber security engineering, architecture and executive leadership across both private and government sectors globally.
Sekuro’s Zero Trust Strategy is a comprehensive, rational, technical cyber security review that will include detailed interviews and assessments of your organisation against 140+ security controls, which takes approximately two weeks to complete. Speak to us today on how we can help your organisation on their Zero Trust journey, and further streamline your cyber security program using our Zero Trust Strategy.

