In the complex landscape of cyber security, safeguarding sensitive information and ensuring regulatory compliance are paramount. The Common Control Framework (CCF) emerges as a comprehensive solution, providing a structured set of internal security controls derived from various security frameworks. These controls are essential for organisations undergoing assessments or adhering to compliance requirements to maintain certifications.
The CCF draws from well-established security frameworks such as PCI DSS, ISO 27001, ISM, SOC 2, NIST CSF, HIPAA, MAS TRM, FedRAMP, and ISMAP. Implementation of the CCF enables organisations to meet compliance requirements, which are crucial for maintaining robust security certifications.
Benefits of the CCF for Organisations
Alignment of Knowledge and Expectations
Implementing a CCF fosters alignment across organisational teams, offering a holistic view of regulations and standards. This alignment ensures that stakeholders are on the same page regarding regulatory requirements, producing more effective risk management.
Increased Order and Organisation
The CCF streamlines individual controls, aligns them with identical requirements, and consolidates them into a singular set. This organisation reduces operational disruptions and facilitates efficient evidence collection, allowing for a more seamless compliance process.
Tailored to Individual Organisation and Security Needs
The CCF is not a one-size-fits-all solution; it can be tailored to meet the unique security needs of each organisation. This customisation enhances efficiency and provides a comprehensive overview of an organisation’s cyber security posture.
Efficient Compliance Tracking
The CCF offers a streamlined approach to tracking compliance and control implementations for multiple security frameworks simultaneously across the organisation.
Implementation of a CCF
The initial phase of implementing a CCF involves gaining a foundational understanding of the risks that the organisation must manage and the compliance requirements it needs to adhere to. Additionally, it is crucial for the organisation to comprehend the criticality and vulnerability of its systems and the data it holds.
Subsequently, the organisation must formulate a set of internal controls that addresses the necessary mitigation practices for the identified risks. These controls should encompass both the corporate governance and technical aspects of the organisation, including its products and services. It is considered a best practice to derive these controls from frameworks already implemented and certified by the organisation or those it aspires to achieve certification. This approach ensures a more precise mapping of controls.
Once the CCF is established and adequately caters to the security needs of the organisation, individual controls from various security frameworks are aligned with the organisation’s internal controls.
While mapping external security framework controls to an organisation’s internal CCF is a subjective process, some methods can be employed to ensure that the CCF accurately reflects the intended security practices the organisation needs to implement. Here are some best practices for control mapping:
- Consider the language used by both internal and external controls. Controls using similar language to describe intent are likely to be a good match.
- Avoid attempting to force a control mapping when uncertain. This precaution helps prevent misalignment between the CCF and external frameworks, ensuring that the organisation does not inadvertently fall short of meeting a control despite indications in the CCF.
- Group controls that cannot be mapped together by framework and categorise them separately. This approach ensures that the organisation systematically addresses unique aspects of each framework when required. It also allows the organisation to allocate resources efficiently, avoiding efforts to implement or comply with controls that may not be applicable.
Here are the different Governance, Risk, and Compliance (GRC) frameworks and standards with controls that are similar in intent (see Figure 1).
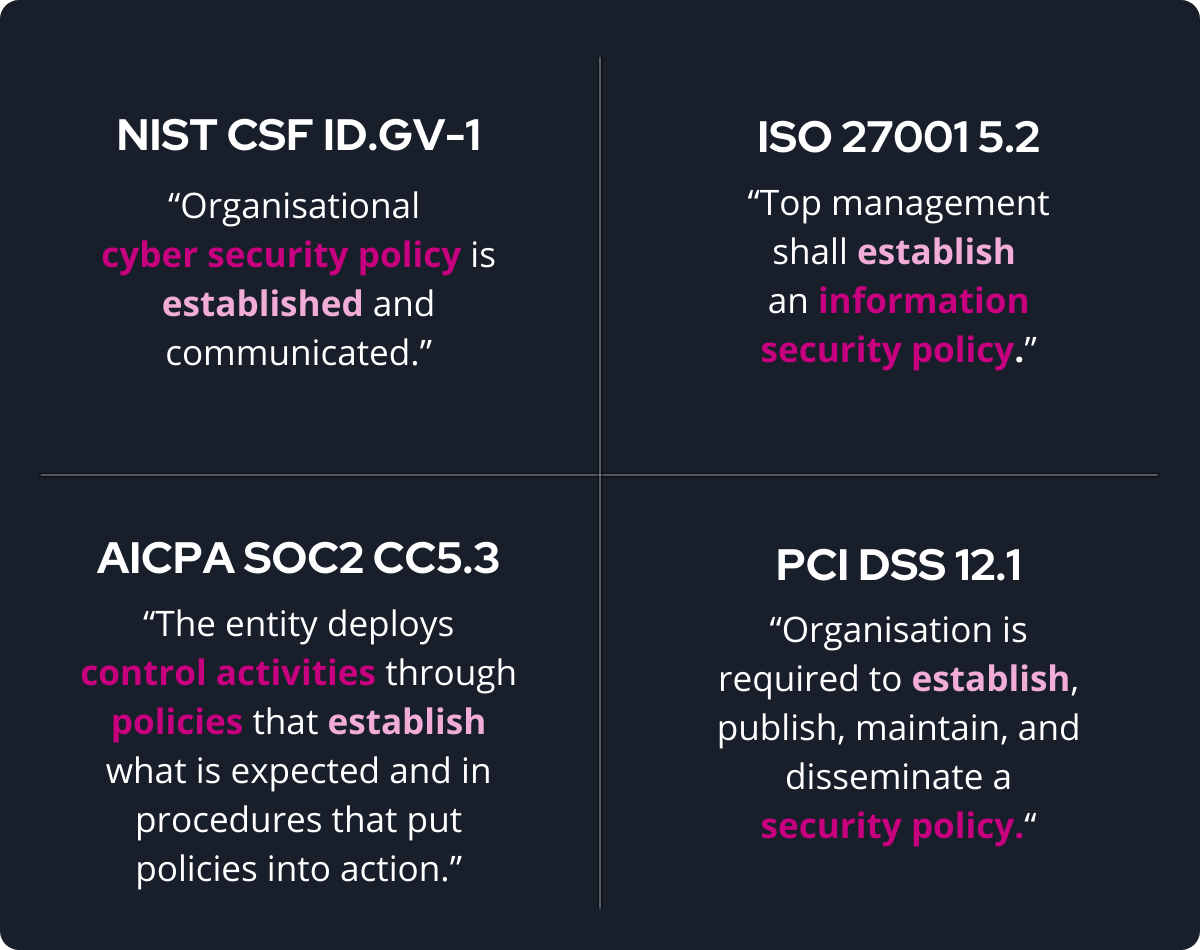
CCF fixes this problem by creating a singular control set and then mapping those controls to the controls in other frameworks that say the same thing. For instance, these four controls above might be mapped to a CCF domain which states that mechanisms exist to establish, maintain and disseminate cyber security and privacy policies, standards and procedures.
About Sekuro’s CCF-as-a-Service
By evaluating each of the control requirements, Sekuro identifies the location where the controls are evaluating the same domain within the organisation. To help maintain an effective governance model for the compliance program, an enterprise-wide GRC automation platform is developed (see Figure 2).
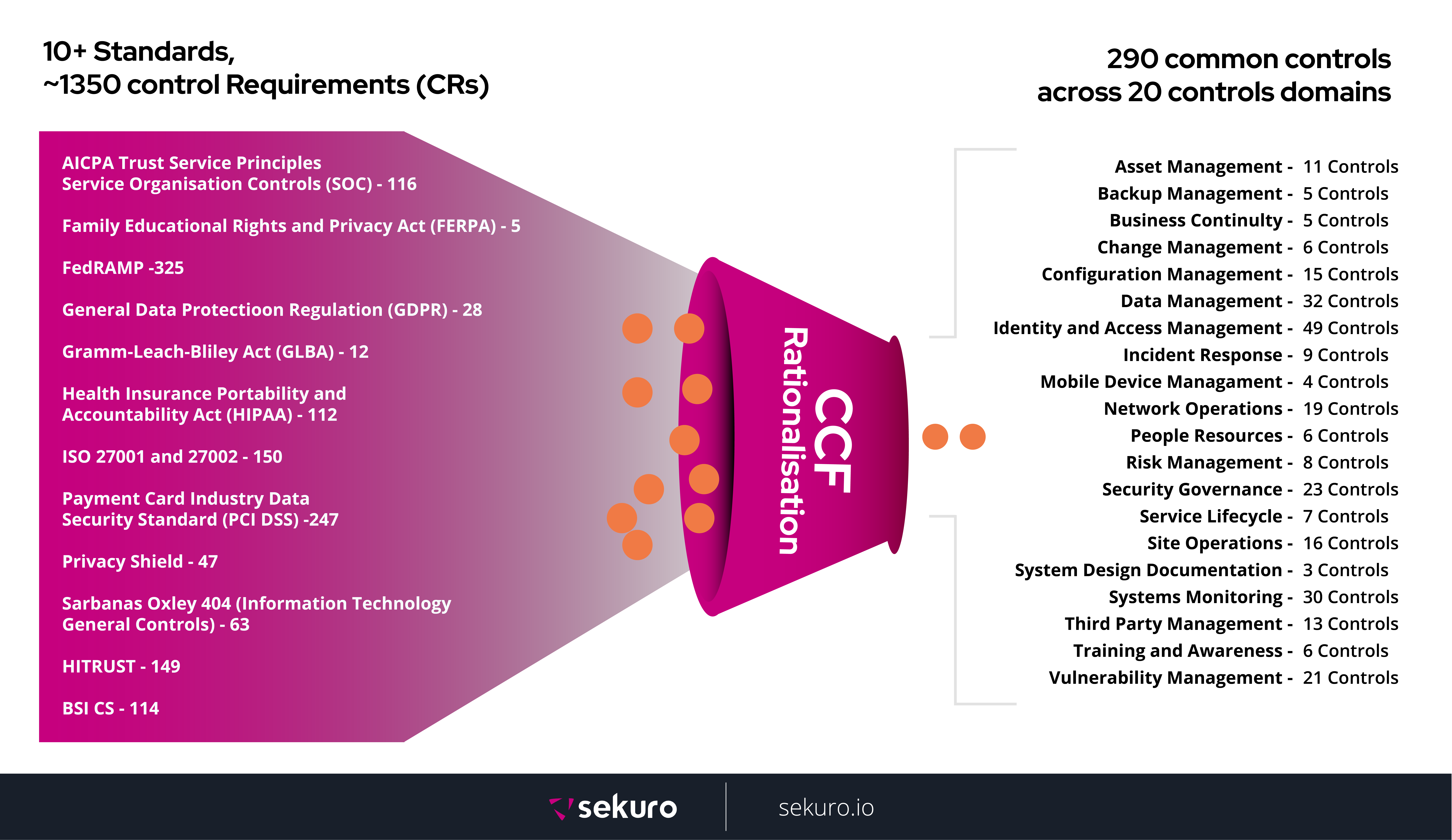
This framework forms the basis of Sekuro’s approach to implementing a CCF for its clients. It involves the following steps:
- Understand the compliance requirements to customise the CCF for the organisation.
- Establish a unified source of truth for risk and control data, simplifying the complexity of compliance management.
- Align evidence with existing frameworks, pinpointing compliance gaps by assessing each control requirement and identifying overlaps between standards. This involves a thorough evaluation of relevant security requirements.
- Formulate a CCF that seamlessly aligns with each standard, ensuring compliance with the pertinent security requirements.
- Create an enterprise-wide GRC automation platform to uphold an effective governance model for the compliance program.
Ensuring the Effectiveness of the CCF
After implementation, organisations will need to conduct follow-up action in order to maintain the effectiveness of their CCF.
- Maintain inventory capabilities: As technology systems and regulatory frameworks evolve, organisations will need to continue taking a thorough inventory of risks and evaluating the controls that are in place.
- Have only one source of documentation: To maximise accuracy and efficiency while minimising gaps, all teams should work from a single source of truth, documenting all work done in a space that is accessible to everyone.
- Incorporate tools for assessing effectiveness: Common controls are only valuable to an organisation if they work effectively. Teams should be able to quickly address deficiencies with minimal labour, in order to avoid increasing the use of resources.
- Carry out continuous monitoring: Organisations will need to stay ahead of problems by constantly monitoring for risks and keeping executives informed of any risks that may arise.
- Adopt rapid reporting: When the organisation’s solution identifies a weak control, they should be prepared and follow a plan of action that is easy as well as comprehensive.
Conclusion
Implementing a CCF is a strategic approach that aligns security controls, ensures compliance, and enhances overall cyber security posture. Contact us to discuss the cyber security strategy that works best for your organisation.

Sita Bhat
Principal Consultant, Sekuro
Sita Bhat is a Principal Consultant at Sekuro, and leads the Governance, Risk and Compliance (GRC) team across various states in Australia - working with numerous global tech giants. Sita is an IRAP Assessor and is passionate about sharing her skills and knowledge, and championed the first GRC related stream inside Sekuro's Hackcelerator program.







