Looking back on 2023 in Cyber Security
It’s 2024 and we now have the benefit of hindsight to look back at 2023 and see what we can learn. The highlights for me were:
- According to the Australian Signals Directorate (ASD), the top 3 causes of cyber incidents in Australia in 2023 were Email compromise, Business email compromise fraud and Online banking fraud
- From Verizon’s DBIR report, we can see that Australia Pacific’s top patterns observed in over 93% of breaches were Social Engineering, System Intrusion, Basic Web Application attacks.
- From IBM’s Cost of a Data Breach report, we see that data breaches have gone up in cost by 2.3% (finally something below inflation!). However over a 3 year period the cost has increased by 15.3%, an annual average of 5.1% (still below inflation though).
- 57% of companies increased the costs of their goods/services after a breach, passing the costs onto consumers.
- It takes 277 days on average to identify and contain a data breach.
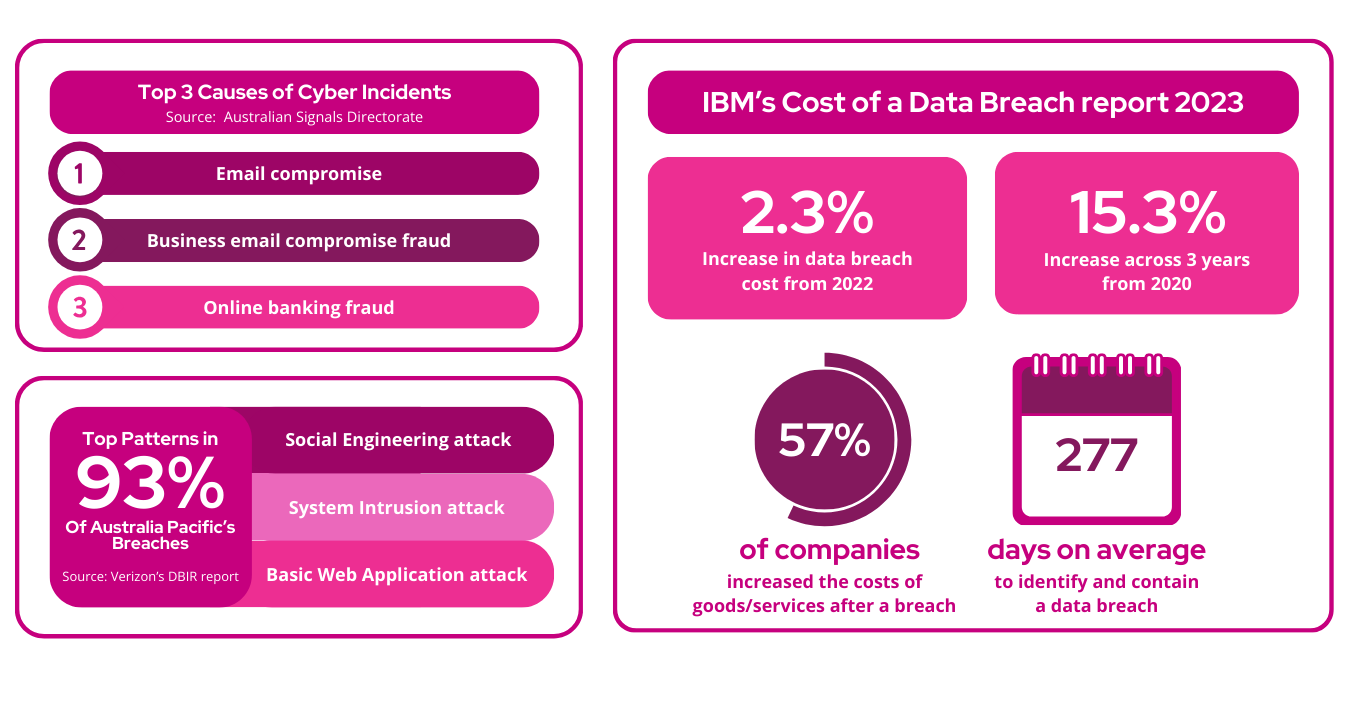
So overall, we see things are the same or getting slightly worse. Is it because organisations aren’t spending enough? I don’t believe that’s the case. Gartner has shown that globally, organisations spent 14.2% more on cyber security than the previous year.
Executives are no longer asking “Why do we need to spend money on cyber” and are instead asking “How much money do you need to reduce our risk?”
The support is there, and the money is there too.
So why are breaches not reducing by the amount we’re spending? Why is it still the basics like email compromise, web application attacks and social engineering that are getting us each year?
I believe it’s because our systems, users, data, and assets are much harder to reach and protect than ever before. The perimeter has expanded, our attack surface is far larger and many of our existing technologies/security controls just cannot keep up. To address this, it’s time to modernise our security strategy.
Our security strategy must embrace and adapt to the modern technology world and threat landscape, and we must enable secure digital transformation.
What does ‘modernising security’ mean?
Modernising security means understanding and accepting that our organisations have evolved. In today’s world, data, users, and devices operate without the constraints of time or location. There’s a constant risk of attackers getting inside our SaaS, PaaS, IaaS, User Endpoints, and on-premises systems at any moment, challenging the traditional idea of securing a fixed perimeter.
It’s crucial to recognize that technology initiatives are no longer limited to IT departments, and valuable data can be found outside secure data centres, sometimes in less secure places. Unlike the past, applications are no longer solely housed in data centres; they are spread out. Modern security should align with the goals of digital transformation, supporting progress instead of creating obstacles.
In summary, modernising security is about dealing with a much broader range of potential attacks and adapting to the fact that organisations now seek more freedom than ever in their operations. It’s about securing data, users, and technology in a world that’s constantly changing and interconnected far and wide.
Why do we need to modernise our security?
Australian organisations need to update their cyber security strategies to keep up with the ever-changing digital threats. The old-school approach of treating our digital space like a castle with walls isn’t cutting it anymore. The rules have changed, and the traditional defences that used to work well are falling short against today’s savvy cyber adversaries.
A big reason for needing a more modern security strategy is that simply shutting down innovative business technologies or restricting access can backfire, turning security into a roadblock for business. This leads to the risk of losing a security team’s most important defensive weapon – which isn’t a tool or technology – it’s their power of influence within an organisation. In today’s world, where collaboration and innovation are key, being too strict with security measures can slow down business growth, make it harder to implement controls and slow down business cases to adapt to new cyber threats – which we can simply no longer afford.
Turning security into a roadblock for business... leads to the risk of losing a security team’s most important defensive weapon – which isn’t a tool or technology – it's their power of influence within an organisation.
On top of that, the bad guys have gotten smarter, and dealing with the complexity of old security methods is leaving organisations vulnerable. Complexity is security’s worst enemy (next to attackers of course), because too many alerts, constant patching, and dealing with outdated tech make our security architecture confusing. This not only makes it harder to spot threats in reasonable time but also increases our operational costs and ability to enact positive change. Studies show that sticking with overly complex security architectures can cost organisations around 31.6% more in the event of a data breach, adding up to a hefty USD 1.44 million burden.
Modernising cyber security strategies isn’t just about using the latest tech; it’s a strategic must-do. It’s about finding the right balance between encouraging innovation, keeping things running smoothly, and building robust defences against the ever-growing range of cyber threats. It’s a shift towards being proactive, flexible, and covering all the bases to handle the dynamic digital landscape in Australia, ensuring that organisations stay resilient against the constantly evolving world of cyber challenges. Essentially, it’s about being secure, adaptable, and seamless all at once.
The ingredients of a modern security strategy
So what ingredients do we need in our recipe to cook up a modern security architecture & strategy? Below are the ingredients/themes we think organisations should look to in 2024 and beyond. These are high level explanations only and we’ll be expanding upon each in upcoming content:
Leading with an Identity-driven access strategy
Identity is the heart of our organisations now, it used to be our Network but due to the perimeter dissolving, Identity is the security control that sits in front of all our valuable assets. Organisations should ensure they have robust identity systems, centralised identities, consistent and adaptive access policies and make sure they have an Identity-focused roadmap with dedicated resources to execute – because strong Identity takes time and needs the right focus.
Addressing the expanded attack surface
The move to Cloud has spread our assets far and wide, attackers find vulnerabilities/assets before we can, and misconfiguration risk is at an all-time high. Organisations should look beyond waiting for the next penetration test to find the surprises and move into continuous asset discovery methods plus using automated monitoring and healing of misconfigurations.
Making security perimeter-less
Any security control that only works effectively in certain places (such as policies/tools that require on-prem or VPN connectivity) need to be earmarked for retirement. Security should be the same in terms of visibility, protection and control of any user, any device, any data, anywhere.
Enabling secure digital transformation
We must enable our business securely, have empathy towards the business impact of cyber security controls and enable secure digital transformation through fair and reasonable policies. How can we do this without the added risk that usually brings? Through in-depth context, so our systems and engineers can make the right decisions at the right time based on the right context. We’re now seeing trends of security being able to improve user experience rather than reduce/maintain it as well, particularly around approaches such as Zero Trust.
Modern threats need modern defences
There has been some amazing technology released in the last 5-10 years that has certainly made our security team’s life easier. But we must never rest on our laurels. The pioneers in our industry will always remember a time where a problem looked ‘solved’ and then the attackers pivoted, and it came right back to bite us. Our tried-and-true security mechanisms are starting to be bypassed again, MFA through AITM (Adversary-in-the-middle) attacks, EDR (Endpoint Detection and Response) bypasses built into malware, malicious emails getting through our secure gateways. We must take our security to the next level, practice defence in depth and stay ahead of attackers. Remember that “out of the box” only gets us so far in our security toolbelt.
Closing Words
The ever-shifting conditions of cyberspace undoubtedly represent challenges for many organisations’ cyber security teams, but they also represent enormous opportunity. We see previous controls that were difficult to implement such as application control, network segmentation, external remote access, identity governance and cloud workload security become possible and far easier to implement than ever before. We see Artificial Intelligence having real tangible value to increase defences around risk scoring, efficiencies in threat hunting – meaning cyber security teams can do more with less. To top it all off, we are seeing that security can make the user experience more seamless for an organisation with reduced cost and complexity – something nigh impossible in the past without added risk. The time is now to implement a modern, robust security architecture – for it is now within reach of any organisation of any size.

Lee Roebig
Customer CISO, Sekuro
Lee is an experienced Cyber Security professional with 16+ years in the technology Industry. He has previously worked in cyber security leadership and architecture roles inside multiple global organisations prior to joining Sekuro. At Sekuro, Lee helps clients with Cyber security strategy, Zero Trust, Virtual CISO, mentorship, executive advisory and security architecture. He has worked with numerous clients on cyber security strategies across industries such as health, insurance, construction, manufacturing, leisure including multiple ASX listed companies.







